Hulud and the Quiet Return of Install-Time Supply-Chain Attacks
- Customer Service
- 21 hours ago
- 2 min read
The Shai-Hulud supply-chain attack was a reminder that many modern compromises don’t rely on exotic exploits — they rely on trusted dependency installs quietly making outbound network calls.
The attack involved malicious open-source packages that executed install-time scripts (postinstall, setup.py) to selectively fetch second-stage payloads, often only when running in CI environments, and then exfiltrate credentials or environment data.Phylum’s analysis shows how little static scanning or CVE-based tooling helps against this class of attack:
Why this class of attack keeps working
Install-time egress is:
Expected (package managers legitimately download things)
Implicitly trusted (few teams monitor outbound traffic during installs)
Poorly attributed (logs rarely say which dependency accessed the network)
This pattern is not unique to Hulud. Variants of it appear in:
Dependency confusion attacks
Typosquatting packages
Malicious postinstall hooks in npm / PyPI
CI-targeted credential harvesting campaigns
A pragmatic mitigation: CI egress allowlisting
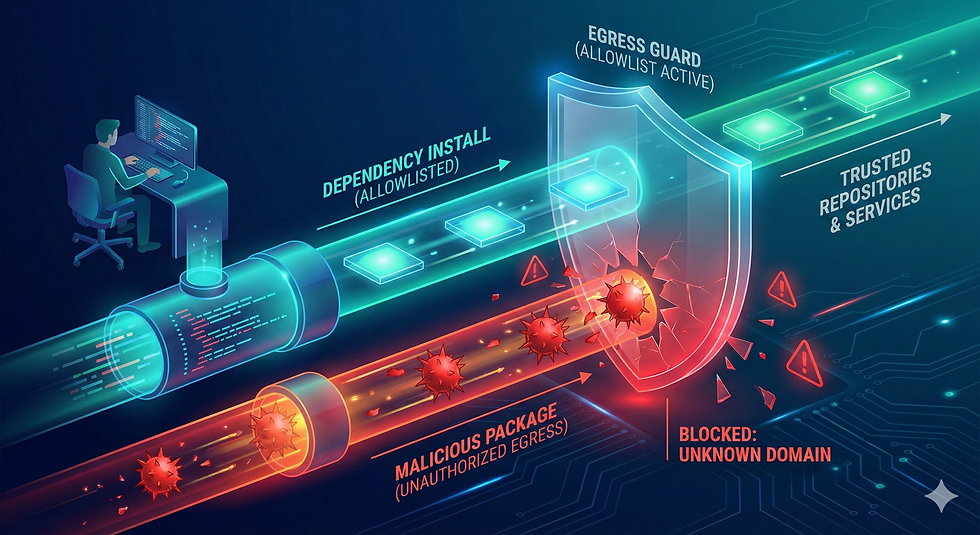
One of the few defenses that reliably stops this entire class of attacks is network egress control during CI:
Allow only known, expected domains (registries, GitHub, artifact storage)
Log or block everything else
Do it during dependency installation, not after
To make this easy to adopt, I built a GitHub Action implementing CI egress guard:
Simple bash-based enforcement
“Dry-run” mode to discover required domains safely
No agents, no SaaS, no runtime dependencies
You can try out the action here:👉 GitHub Action: CI Egress Guard
Why this matters beyond Shai-Hulud 2.0
Egress allowlisting doesn’t just catch known malware — it removes the attacker’s ability to evolve:
Second-stage payloads can’t be fetched
Credential exfiltration fails
CI becomes a low-value target
This approach complements SBOMs and policy scanning by adding runtime enforcement — something most SDLC security stacks still lack.
If you’re serious about supply-chain security, watching what your CI talks to is no longer optional.




Comments